MIPC Camera Firmware Vulnerability
OS Command Injection Vulnerability
Aug 2024 - Joern
1. Abstract
Cameras using the MIPC camera framework host a HTTP service on port 80 to provide a communication channel with other entities (i.e. smartphone app) via a proprietary protocol. One of the functions offered by this service will process input without performing an authentication. Furthermore there is no input validation implemented and parts of the user-controlled data is used as input for an OS shell command. An attacker on the same network can use this vulnerability to inject arbitrary OS commands which will be executed as root user. Via this injection channel the attacker is able to change the root password and open a telnet service in order to access the root console.
The vulnerability has initially been discovered in the Annke Crater 2 Camera. The used MIPC camera framework developed by MIPC Technology Co.,LTD / Shenzhen Fujikam Industry Development is also used by other vendors. Therefore devices of other camera brands using this MIPC framework might be affected by this vulnerability as well. No further information was provided by MIPC / Fujikam as of now.
Relevant CWEs:
- CWE-306: Missing Authentication for Critical Function
- CWE-78: Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’)
The following description of the vulnerability will mainly focus on the generic nature of the vulnerability as to not expose too much information on how to gain root access on the device and therefore protect users of the affected cameras.
All information was shared within a responsible disclosure process with the Annke Support Team and MIPC/Fujikam Support Team.
2. Device under Test
The research has been conducted with following device:
- Annke Crater 2 (F300) MIPC Firmware Version v5.4.1.221222153318
3. Potentially Affected devices
Since not only the vendor/manufacturer Annke is using this MIPC framework, cameras of other brands might also be affected by this vulnerability.
According to web research following brands are using the MIPC camera framework:
- ANNKE
- SANNCE
- INKERSCOOP
- KAMEP
- COOAU
4. Vulnerability Description
The vulnerability can be exploited by invokating the “ccm_debug_m” function with specifically crafted parameters. An attacker is able to access a specific sub-function provided by “ccm_debug_m” function since it is currently not included in the user authentification process. This sub-function is invoking an OS command using unvalidated user-controlled input as a parameter. Since the process is running as root, an attacker can inject arbitrary OS commands which will be executed by the underlying Linux OS.
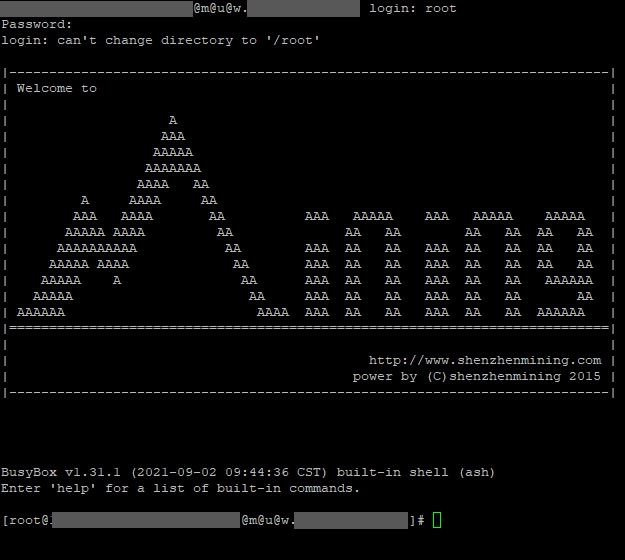
In order to access the root shell and gain code execution on this device, the attacker needs to change the password of the root user and start a telnet service. By injecting commands to change the root password and start the telnet service via a crafted HTTP request, the vulnerability can be exploited.
After telnet login the root shell is available:
5. Vulnerability Remediation
A mandatory authentication scheme should be put in place for all functionality within the function “ccm_debug” / “ccm_debug_m” to mitigate unauthorized exposure of camera services. Additionally, an appropriate input validation scheme should be implemented to prevent an attacker to inject malicious OS commands. As further defense-in-depth measure it should be considered to run the relevant process in a non-privileged user mode.
6. Responsible Disclosure
All information on the vulnerability including a PoC was shared in a responsible disclosure process with the Annke Support team & MIPC Support Team. The prompt e-mail responses, professional incident handling is much appreciated and shows that Annke and MIPC are taking customer security serious. The PoC will not be made available to the public to ensure customer privacy.
Timeline:
- 2024-03-17: Initial Contact
- 2024-03-18: Response of Annke Support Team
- 2024-03-20: Provision of Report & PoC
- 2024-05-03: Issue confirmed by Annke Support Team and testing of fixed version by MIPC R&D team
- 2024-05-30: Fix available to customer
- 2024-06-10: Provision of draft version of public report
- 2024-06-15: Application for CVE-ID
- 2024-08-09: Release of public report on Github
7. Further References
- CVE Record (CVE-2024-39091): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-39091